Cyber Security
Protecting Infrastructure — Reducing Risk — Ensuring Compliance
- Comprehensive Protection
Multi-layered defense covering network, endpoint, cloud, and data.
- Advanced Threat Detection
AI-powered monitoring to identify and stop zero-day attacks, malware, and intrusions.
- Compliance & Governance
Ensure adherence to regulatory standards (GDPR, ISO, NTRA, etc.).
- Resilience & Business Continuity
Built-in redundancy, backup, and disaster recovery for uninterrupted operations.

- Building a Cyber-Resilient Enterprise
At Internetwork Technology, we provide end-to-end cybersecurity solutions that safeguard your digital assets against evolving threats. Our vendor-agnostic approach means we design security strategies tailored to your environment, combining best-in-class technologies from multiple vendors to ensure maximum protection, compliance, and resilience.
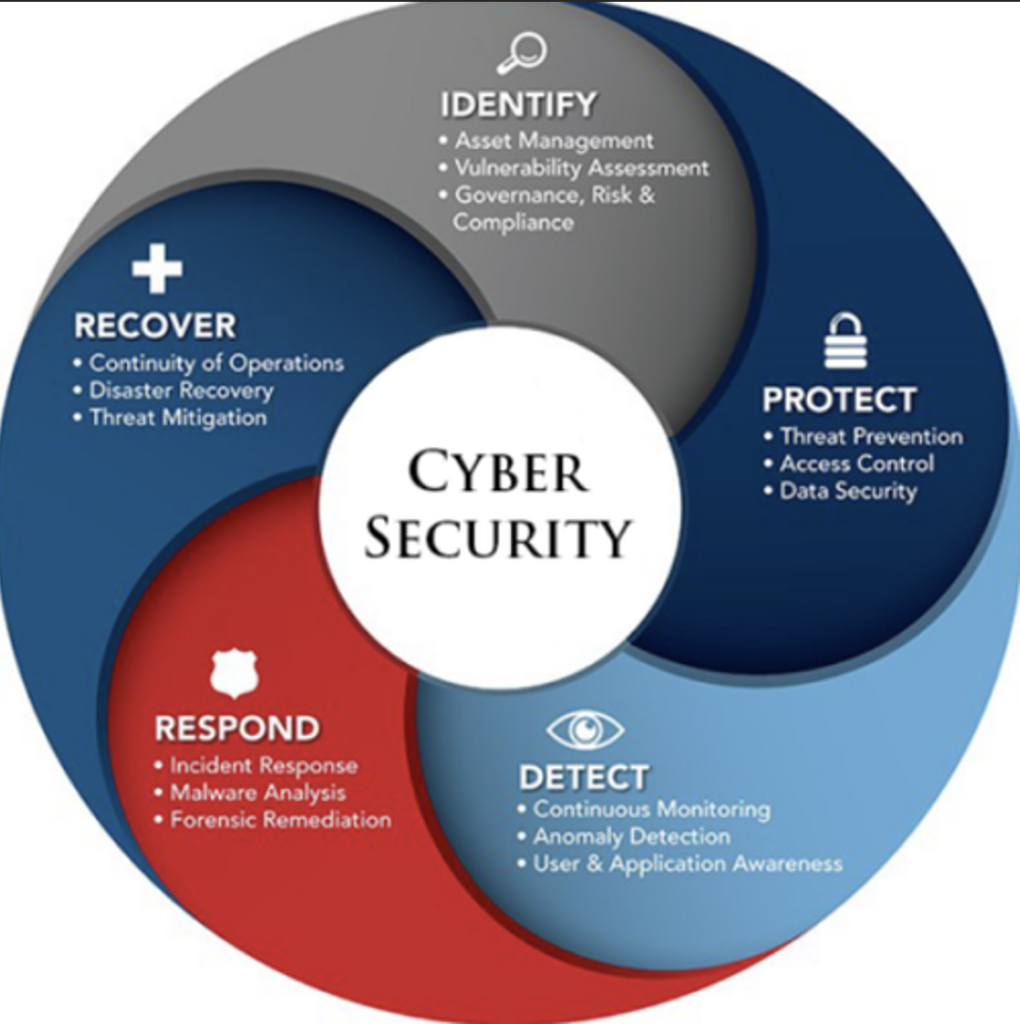
Security Strategy (Aligned with NIST Cybersecurity Framework)
- Identify – Understand risks across assets, data, and systems.
- Protect – Implement safeguards such as access control, encryption, and secure configurations.
- Detect – Continuous monitoring and analytics to identify threats in real time.
- Respond – Automated and manual response mechanisms to contain incidents.
- Recover – Plans for resilience, backup, and restoring services after an incident.
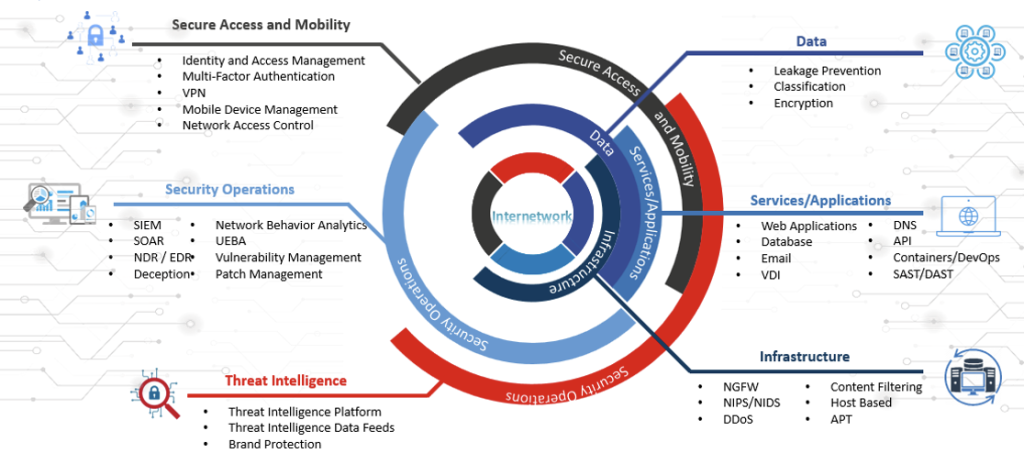
Security Framework Coverage
- Secure Access & Mobility: Identity & Access Management, MFA, VPN, Mobile Device Management, NAC.
- Security Operations: SIEM, SOAR, NDR/EDR, UEBA, Vulnerability & Patch Management.
- Threat Intelligence: Threat feeds, brand protection, and deception technologies.
- Data Security: Leakage prevention, classification, and encryption.
- Applications & Services: Security for web apps, databases, APIs, containers, DevOps pipelines.
- Infrastructure Protection: NGFW, IDS/IPS, DDoS defense, APT protection, and content filtering.
- Business Benefits
- Stronger Security Posture – Multi-layered defense across endpoints, data, and networks.
- Compliance & Risk Management – Alignment with global standards like GDPR, ISO, NIST.
- Operational Continuity – Built-in redundancy, failover, and disaster recovery.
- Future-Ready – Flexible approach that adapts to new vendors and emerging threats.
- Industries We Protect
- Finance & Banking – Regulatory compliance and real-time fraud protection.
- Healthcare – Secure patient data and protect critical applications.
- Government & Defense – National-level compliance and cyber resilience.
- Manufacturing & Industry 4.0 – Protect IoT, SCADA, and connected environments.
- Hospitality & Retail – Secure customer data and transactions across distributed sites.
- Why Internetwork Technology?
Unlike vendor-locked solutions, we design holistic cybersecurity strategies by combining leading technologies from multiple partners (currently Fortinet, Trend Micro, and more to come). This ensures our clients always receive the best protection available, tailored to their needs.
Our approach, Trusted Innovation. Controlled TCO., ensures your organization achieves the right balance between security, compliance, and cost efficiency.
Protect Your Business Before It’s Too Late
